This week
- US ATC runs on Win95, floppy disks
- DarkGaboon victimising Russian companies with ransomware
- Google Cloud outage caused by poor API engineering
- Google account recovery flows exposed name, phone number
- Disruption at Whole Foods distributor following cyber attack
- M&S online orders resumed
Interesting stats
15x increase in the cost of typical security incidents today, compared to 2008, with $603K the median loss, and $32M the 95% percentile loss for their data from 2015 to 2024:
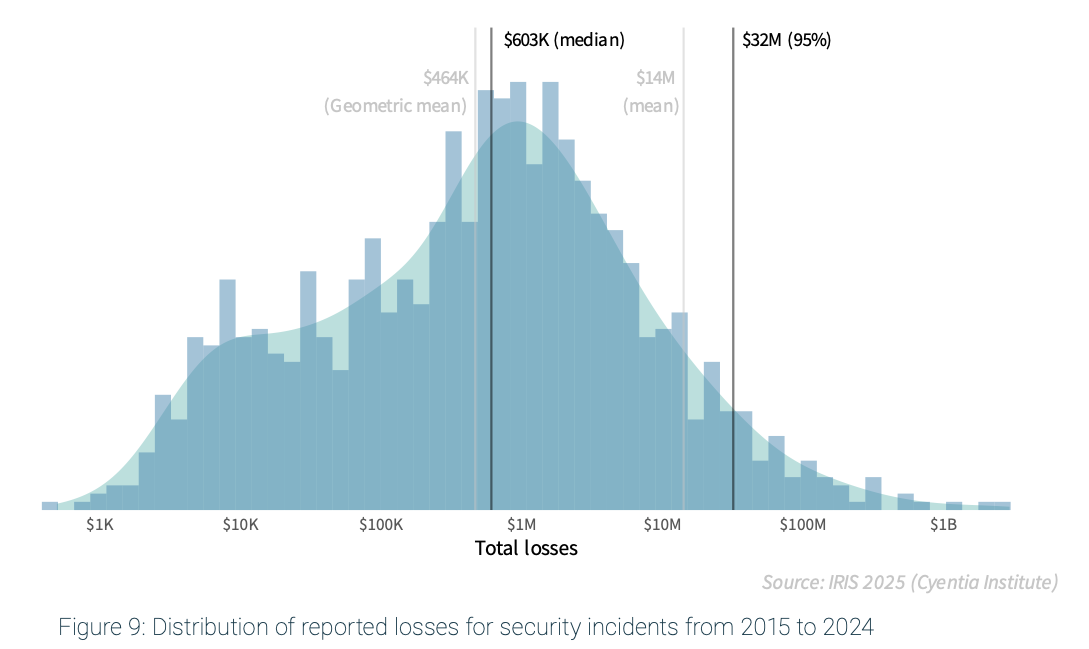
4.75x increase in 90th percentile losses, and 15.20x increase in 50th percentile losses over their last 15 years of data. LINK, REPORT (PDF)
Five things
-
United Natural Foods (UNFI), the primary distributor for Whole Foods, experienced a “nationwide technology system outage” that’s been attributed to a cyber incident. The attack has impacted UNFI’s ability to ship items from its warehouses, and items are unavailable in some stores. UNFI operates 52 distribution centres that get goods from 11,000 suppliers to 30,000 stores in North America. In an earnings call on Tuesday, CEO Sandy Douglas declined to update its financial outlook, citing an ongoing assessment of the cyber attack’s impact. UNFI is the latest attack against retail sector organisations in the last few months, with cybercriminals targeting M&S, Co-Op, North Face, and others. UNFI, MORE, EARNINGS
-
Google recovery phone numbers could be retrieved without alerting their owner. Google’s now fixed the issue. Security researcher skull discovered that it was possible to brute force Google account recovery options to obtain the phone number and name associated with an account. This could ‘unmask’ an otherwise anonymous user or represent a privacy issue for any user. The issue stemmed from being able to play off both the standard account recovery workflow and a mechanism for users that have JavaScript disabled. The proof-of-work captcha in the JavaScript version could be repeatedly replayed to the non-JS version, allowing the phone number to be determined. For UK format numbers, the process takes just 4 minutes, and there are no notifications to the victim. RECOVERY, MORE, BLOG POST
-
A new group dubbed DarkGaboon has been targeting Russian companies with ransomware. Positive Technologies, a Russian cyber firm, says the attacks have been against banking, retail, tourism, and public services sectors, and initial access is usually via phishing emails to employees in the finance department. If successful, DarkGaboon deploy the LockBit 3.0 malware to encrypt the files of the victim organisation; no data exfiltration has been observed. With many cybercrime groups being based there, it’s unusual to see Russian companies being targeted, and I suspect that lack of attention means there are some vulnerable targets. DARKGABOON
-
M&S resumed online orders, six weeks after an attack that forced the UK retailer offline. The company will restore click-and-collect, special, and international delivery options in the coming weeks. M&S shares are up 4% (though this isn’t a good way to measure the cost of an incident). In an excellent (though rare) example of competitors pulling together in a time of crisis, Tesco subsidiary Booker says it’s been sending extra stock to M&S and Co-Op stores to keep branded products stocked while both suffered disruption to their ordering systems. M&S, BOOKER
-
US Air Traffic Control is run on Windows 95 and floppy disks. Chris Rocheleau, head of the Federal Aviation Administration, has been telling a House committee that they want to replace the system over the next four years. Windows 95 would be 29 years old at that point. It’s an example of a tried and trusted system that is common amongst critical safety use cases that must be available 24/7. The out-of-support software is heralded as the unlikely saviour from last year’s CrowdStrike outage. You’d certainly never get Cyber Essentials certification, though. ATC
In brief
-
⚠️ Incidents: Salesforce’s Heroku platform-as-a-service offering suffered a six-hour outage affecting developer logins and some platform functionality. Fortune 500 insurer Erie Insurance has suffered disruption this week attributed to “unusual network activity” that necessitated the company “take protective action for the security of our systems”, per an SEC 8-K filing. NHS Professionals, a company set up by the Department of Health and Social Care to provide temporary staff to NHS trusts, suffered a breach in May 2024 that was previously unreported. Insiders suspect the attacker’s objective was to ransom the organisation, but it was thwarted with attackers making off with ‘just’ the Active Directory database. Yes24, a large South Korean ticketing and entertainment industry company, suffered days of outage this week, resulting in the cancellation and postponement of events. Google Cloud suffered an outage this week that also affected some of Cloudflare’s services. Remarkably, Google says that an update to its API control pane was “never exercised” (tested) in a rollout, wasn’t behind a feature flag (used to control the adoption of changes), and did not have “appropriate error handling” that resulted in crashes when the function encountered blank fields in data. All in all, it sounds like amateur hour, but props on the incident report. Four Financial Conduct Authority (FCA) staffers were let off with warnings for emailing regulatory data to their personal email accounts. HEROKU, ERIE, NHS PROFESSIONALS, YES24, GOOGLE/CLOUDFLARE (INC REPORT), FCA
-
🕵️ Threat Intel: Write up about The Com, the loose collective from which groups like Scattered Spider, Oktapus, LAPSUS, hail, and how infamy drives their attacks against the likes of MGM Resorts, Snowflake, and M&S. Realiquest says Scattered Spider is currently trying social engineering techniques against IT MSPs (managed service providers). DomainTools says that FIN6 targets recruiters by impersonating job seekers and sending malware-laden resumes to infect them with the ‘More Eggs’ malware. THE COM, MSPs, FIN6/RECRUITERS
-
🪲 Vulnerabilities: A recent vulnerability in Roundcube, an open-source webmail platform, is being actively exploited. Over 80,000 instances are still vulnerable to CVE-2025-49113 (9.9/10), a critical remote code execution bug. Ivanti has fixed three hardcoded keys in its Workspace Control (IWC) product: CVE-2025-5353, CVE-2025-22455, and CVE-2025-22463 (8.8, 7.2, 8.8/10 respectively) allow locally authenticated attacks to decrypt credentials. Microsoft Copilot was susceptible to a critical, zero-click vulnerability (CVE-2025-32711; 9.3/10) that could have seen information exposed by a user receiving a specially crafted email. Microsoft says no customers were affected by the issue. ROUNDCUBE (ADVISORY), IVANTI (ADVISORY), COPILOT (ADVISORY)
-
🧿 Privacy: 404 Media reports that Airlines Reporting Corporation (ARC), an airline industry-owned data broker and transaction processing company, sells flight traveller data to the US Immigration and Customs Enforcement (ICE). Notably, their contract requires ICE not to name ARC as the source of the information. It’s not the first time ARC’s been in the press: previous exposés have shown the DOD purchasing data. Spyware vendor Paragon says it’s terminated its contract with the Italian government over allegations the country used its technology to spy on a journalist. It’s odd (refreshing?) to see a spyware company holding its customers accountable. ARC, PARAGON
-
📜 Policy & Regulation: The EU is stepping up its efforts to reduce reliance on US cyber security programmes, such as the vulnerability database delivered by MITRE that came close to running out of funding earlier this year. WhatsApp is throwing its weight behind Apple’s case against the UK Home Office’s technical capability notice (TCN) requiring it to ‘backdoor’ its Advanced Data Protection system. EU, WHATSAPP
-
👮 Law Enforcement: An international law enforcement operation, Operation Secure, led by Interpol, has arrested 32 people and notified 216,000 victims of infostealer malware. Singapore authorities have led the multi-national Operation Frontier+ to shut down dozens of scam centres and arrested over 1,800 people tied to the theft of $225 million. OP SECURE, OP FRONTIER
-
💰 Investments, mergers and acquisitions: Data protection outfit Cyera closed a $540 million Series E round, valuing the company at $6 billion. Guardz, an MSP-focussed detection and response platform, has raised $56 million in its Series B round. CYERA, GUARDZ
-
🗞️ Industry news: Brett Leatherman has been selected to run the FBI’s cybercrime division. Leatherman is a 22-year agency veteran involved in operations to unmask LockBitSupp and respond to the Colonial Pipeline attack. The House Appropriations Subcommittee on Homeland Security has “responsibly trimmed” CISA’s by $134.8 million, rather than the $495 million requested by the Trump administration. FBI, CISA
And finally
- UK blood donors: The cybercriminal attack last year on Synnovis, a pathology supplier to the National Health Service, meant that stocks of O- blood — the universally accepted blood type — were used because tests couldn’t be completed. A year later, stocks remain low, and the NHS is calling for 1 million people in England to sign up and give blood (just 2% of the population is “keeping the nation’s blood stocks afloat”). LINK, SIGN UP, BOOK AN APPOINTMENT