This week
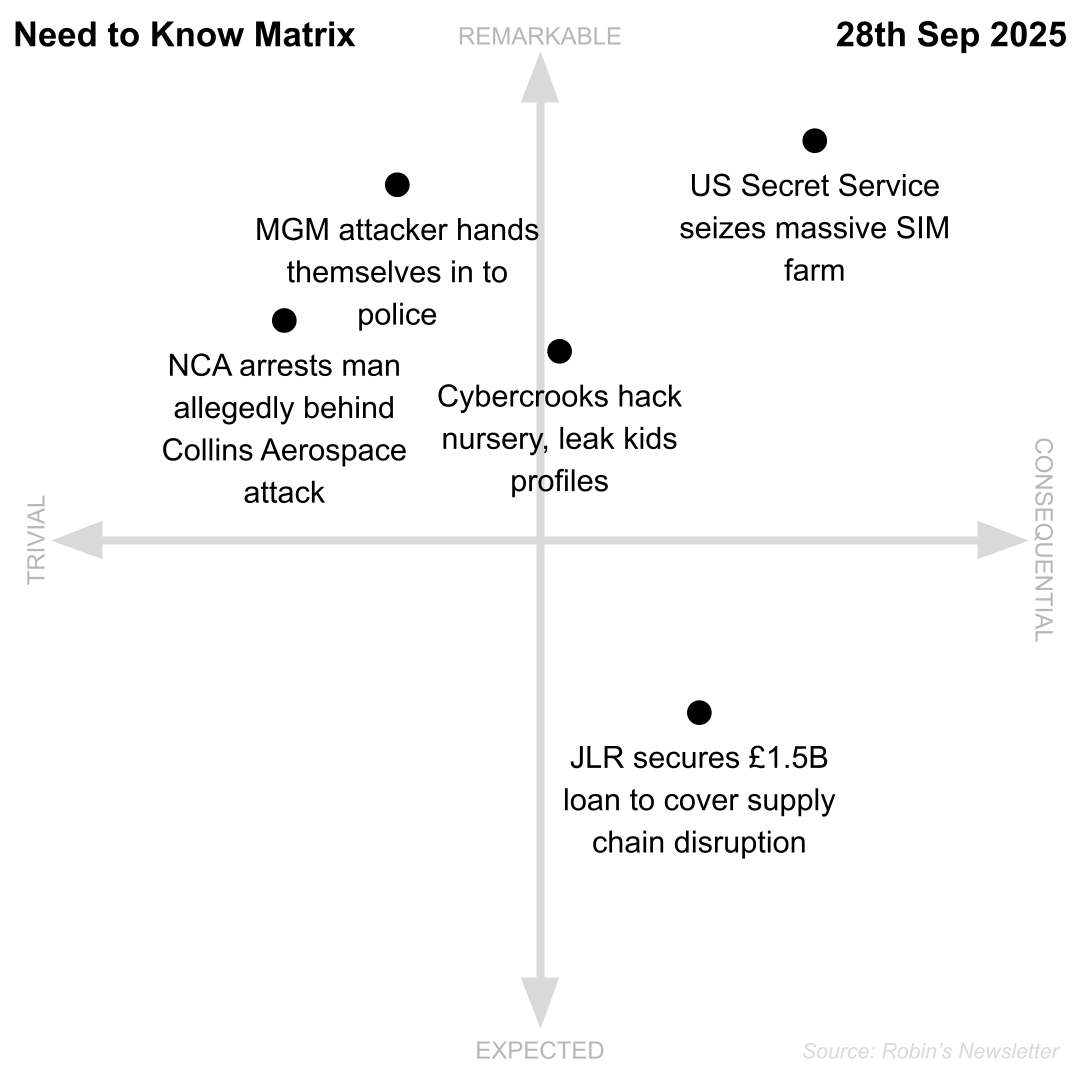
- JLR secures £1.5B loan to cover supply chain disruption
- US Secret Service seizes massive SIM farm
- Cybercrooks hack nursery, leak kids’ profiles
- MGM attacker hands themselves in to police
- NCA arrests man allegedly behind Collins Aerospace attack
Interesting stats
$439 million in cash and cryptocurrency seized by police investigating cyber crimes between April and August 202, according to Interpol. LINK
£206 million revenue the Co-op lost through disruption during a ransomware attack earlier this year, equating to a £120 million hit to full-year profits, inclusive of insurance recovery. LINK
~2% risk reduction from cyber security training, based on an eight-month, randomised controlled experiment of 19,500 employees at US San Diego Health. The authors suggest prioritising MFA and password managers instead of expensive training programmes for better ROI. (H/t Simon) LINK
Five things
- JLR: A couple of attention-grabbing headlines and stories in the ongoing fallout of Jaguar Land Rover’s cyberattack. JLR will bear the full costs of its cyber attack because it had not finalised its cyber insurance cover at the time of the attack. You may see “failed to buy” type headlines; however, it’s rumoured that they were offered £30 million cover for £850K, woefully inadequate for a business of JLR’s size. Eleanor Dallaway (of Assured, a cyber insurer) has a good post on LinkedIn to this end. What’s more, based on Tata Motors’ recent financial reports, JLR has a £3.3 billion cash balance and a further £1.7 billion revolving credit line to draw on (further reinforcing that £30M cover really isn’t a sensible purchase). JLR has also secured a further £1.5 billion line of credit from a commercial bank, which the UK government is underwriting. Worth noting, despite comments on social media, the UK taxpayer isn’t coughing up this money; it’s not costing ‘us’ anything (unless JLR defaults). JLR has begun bringing systems back online and expects operations to resume in early October. Stellantis (which includes the Fiat, Jeep, and Peugeot brands) confirmed that attackers stole customer email addresses and names from a third-party supplier supporting its North American operations. Sounds like a Salesloft breach. INSURANCE, POST, CASH, LOAN, STELLANTIS
Side-note: Quantifying your cyber risk can help you determine if you have the right level of coverage. Cydea (my company) can help you do that quickly and effectively.
-
SIM City: The US Secret Service has seized “more than 300 co-located SIM servers and 100,000 SIM cards” in the New York City area. The “well-organised and well-funded” setup involved “nation-state threat actors and individuals that are known to federal law enforcement”. This appears to be a capability that a nation-state has subcontracted to local organised crime. The Secret Service states that the network could “essentially shut down the cellular network” in NYC by overloading cell towers and telecom networks, and theoretically could have sent text messages to the entire US population in 12 minutes. It’s a slightly odd framing, and I suspect it was more to provide a capability for placing anonymous calls, potentially one-time ‘throw away’ numbers for contacting intelligence assets, or could be useful for registering accounts on various services. It was anonymous calls that led the Secret Service to the discovery, as they were investigating threatening calls to US lawmakers. As 404 Media points out, ticket scalpers also utilise this type of setup to purchase tickets for popular concerts quickly. Potentially a nice side income for the operator. Either way, those 100,000 SIMs will provide a rich treasure trove to mine for intelligence now. SIM FARM, MORE, SCALPERS
-
Kido: A threat group calling itself Radiant has broken into a software platform used by nursery group Kido and stolen the data of 8,000 children. It has begun leaking the profiles — which include names, dates and places of birth, addresses, and phone numbers of guardians, and photographs — on its leak site in a bid to extort a payment from Kido. These attackers are grade-A assholes. KIDO
-
Scattered Spider: Thalha Jubair, arrested last week, was one of two ‘core figures’ in Scattered Spider’s operations, according to security researchers. I suspect that between the UK and US authorities, Jubair will face considerable pressure to provide details on others in the group. Also, last week, a juvenile suspect turned themselves in to Las Vegas police for their involvement in the ransomware attacks on Caesars and MGM casinos. I expect a few more arrests in the coming months as co-conspirators are brought to justice. SPIDER, VEGAS
-
Collins Aerospace: The UK’s National Crime Agency has arrested a “man in his forties” in West Sussex in connection with the cyberattack against Collins Aerospace that caused air travel disruption last week. The attack, against Collins’ ARINC SelfServ cMUSE software, affected check-ins and bag drops at Brussels, Berlin, Dublin, and London Heathrow airports. Collins Aerospace’s parent company, RTX, which also owns defence contractor Raytheon, confirmed in an SEC filing that the incident was a ransomware attack. The arrest is some swift work from the NCA. ARREST
In brief
-
🕵️ Threat Intel: Atomic infostealer is targeting Mac users and being spread by adverts and a fake Lastpass installer. Senior execs at legal, SaaS, and technology companies are being targeted by Chinese government-linked attackers seeking to steal intellectual property with BRICKSTORM malware, according to Google. ATOMIC, BRICKSTORM
-
🪲 Vulnerabilities: Two million Cisco devices with SNMP exposed to the internet may have been exploited using a zero-day vulnerability in the networking giant’s IOS and IOS XE operating systems. CVE-2025-20352 (7.7/10) allows low-privileged users to carry out denial-of-service attacks, while higher-privileged users can achieve code execution. The ‘read-only’ community string is what’s needed to exploit the issue. SonicWall has released a firmware update that can also remove rootkit malware if that device has been infected. SolarWinds has released a hot fix to address CVE-2025-26399 (9.8/10), a remote code execution issue in its Web Help Desk solution that it has tried to fix twice before. Third time’s a charm? The baseband management controller (BMC) in Supermicro server motherboards contains multiple vulnerabilities (CVE-2025-7937 and CVE-2025-6198) that can lead to an attacker gaining “unprecedented persistence”. Some of this is marketing puff from Binarly. Hopefully, it’s not an issue for many, as you’re not exposing your lights-out management interface to anywhere other than a highly trusted administrator network, right? CISCO (ADVISORY), SONICWALL (ADVISORY), SOLARWINDS (ADVISORY), SUPERMICRO (ADVISORY)
-
🧑💻 End user and consumer: 1Password has a ‘travel mode’ that removes unwanted vaults from your device when crossing borders and at risk of device searches. 1PASSWORD
-
🧰 Guidance and tools: Interesting read from CyberScoop on what to do if you realise you’ve hired a North Korean IT worker. N KOREA
-
🛠️ Security engineering: GitHub has announced that it’s making changes to how developers publish packages on the platform, in a move to try and reduce the effectiveness of software supply-chain attacks like s1ngularity and Shai-Hulud. The changes will require multi-factor authentication for publishing, amongst other changes. These updates will remove the automatic publishing of malicious packages, but a worm could still modify code and hope that a developer doesn’t notice when pushing a legitimate update. Postmark-mcp, a model context prompt (MCP) package used by AI agents to interact with Postmark email workflows, was compromised to BCC every message to an attacker-controlled address (h/t Tim). GITHUB, MCP
-
🧿 Privacy: Democrats on the Senate Homeland Security and Governmental Affairs Committee say that Department of Government Efficiency (aka ‘DOGE’) practices “violate statutory requirements, creating unprecedented privacy and cybersecurity risks”. DOGE employees, formerly led by Elon Musk, gained access to a large amount of US federal government data after Trump’s re-election, with multiple whistleblowers saying data was being copied to unknown and unsecured environments. DOGE
-
📜 Policy & Regulation: UK Prime Minister Kier Starmer has revived plans for a Digital ID scheme, with the intention of all legal residents having one by the end of the current parliament (August 2029 at the latest). Job seekers and employers will be required to use the IDs in right-to-work checks. DIGITAL ID
-
🗞️ Industry news: “The problem [is], we suck at patching” said former NSA exec Rob Joyce on the topic of AI vulnerability detection, and the hopes that it will lead to better software security. Things have to get worse before they can get better? JOYCE
And finally
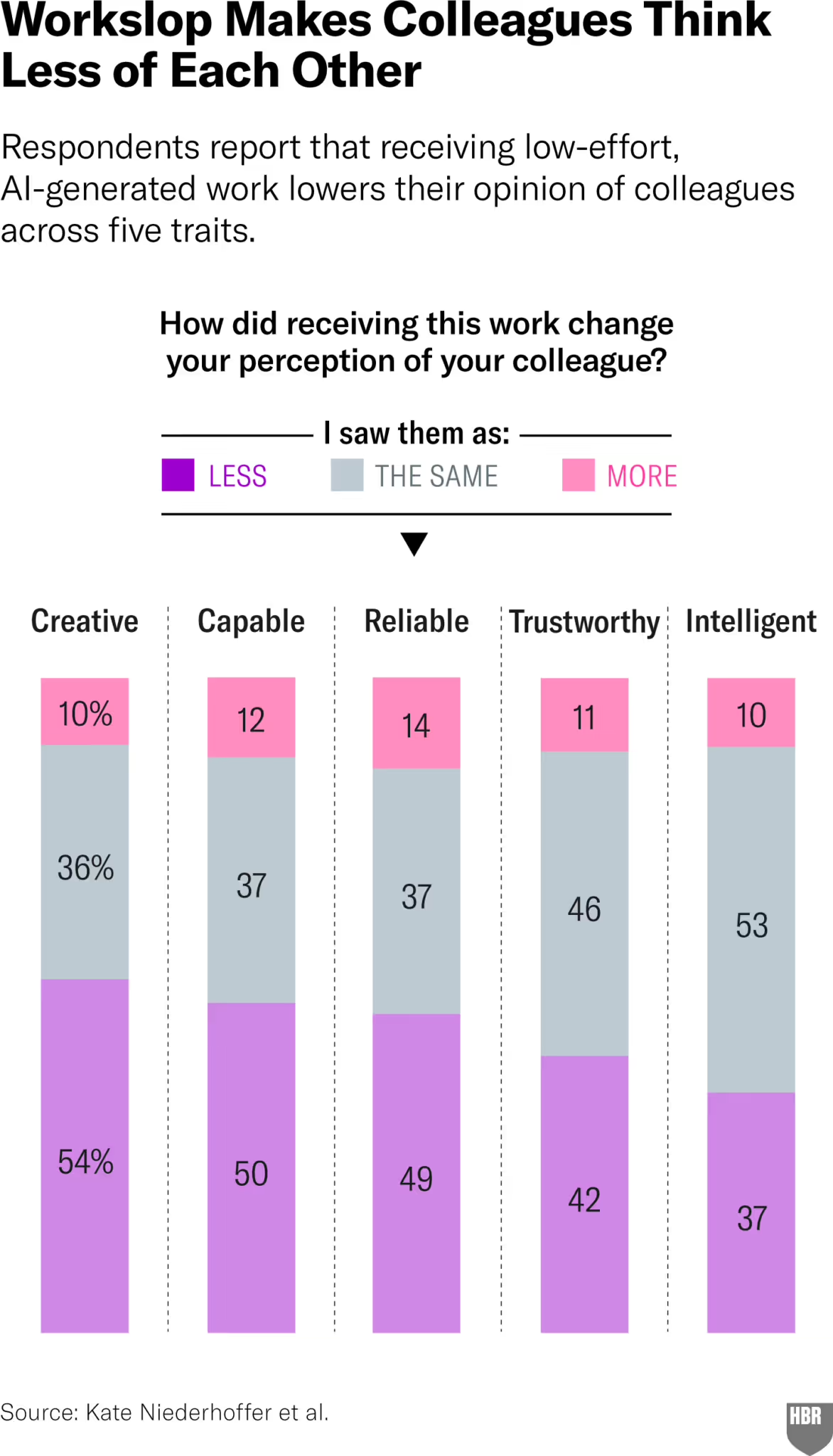
“Workslop” — AI generated work content that masquerades as good work, but lacks the substance to meaningfully advance a given task.
- 95% of organisations are yet to see a measurable return on investments in AI-led processes, with each instance of ‘workslop’ carrying a $186 “invisible tax” as co-workers spend an average of 1h56m dealing with each one, according to this HBR article. Receiving AI generated work reduces perception of creativity, capability, reliability, trust, and intelligence, apparently: