This week
It’s been a busy week, with a couple of different events and a lot of brilliant conversations: it was great to see so many people at RISK Europe, for Niall’s panel, Tim’s AI talk, my panel on aligning cyber risk and business strategy, and, of course, on the Cydea stand. You couldn’t miss us! With some other personal commitments this week, it’s going to be a cut-down edition.
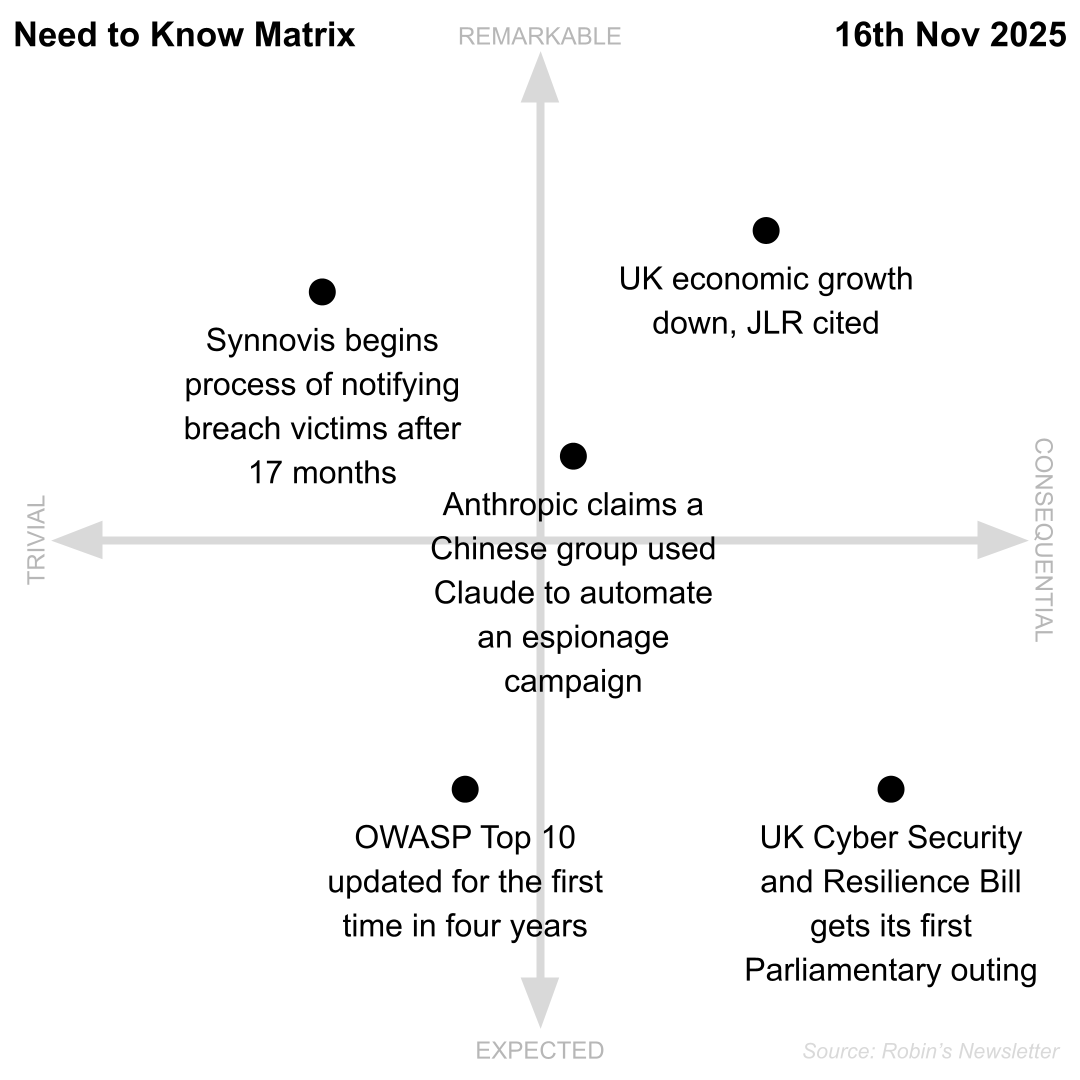
- Anthropic claims a Chinese group used Claude to automate an espionage campaign
- UK Cyber Security and Resilience Bill gets its first Parliamentary outing
- OWASP Top 10 updated for the first time in four years
- UK economic growth down, JLR cited
- Synnovis begins process of notifying breach victims after 17 months
Interesting stats
£197 million paid out for cyber claims in 2024, 3.3x that in 2023 (£60 million), according to the Association of British Insurers. LINK
$244 million received in ransomware by the Akira ransomware gang, say government cyber agencies. LINK
3.73% of web apps tested by OWASP had broken access controls (see below).
Intelligence failure? 83% of organisations* have a dedicated threat intelligence team, with **76%** spending at least $250,000 per year on external TI products (14% spend over $1 million), however **50%** say they have difficulty determining credibility or accuracy, **46%** say the intel products lack context for their specific environment, and **39%** cite slow delivery of time-sensitive intelligence as a challenge with their current vendor. **1/3** overall believe the high cost relative to value received is a challenge, according to Recorded Future’s _2025 State of Threat Intelligence_ report. LINK
* Take this with a pinch of salt: the survey was of 615 respondents, all from businesses with more than 1,000 employees. In the UK, less than 0.6% of all businesses with employees have 250 or more employees!
Five things
- AI espionage: Anthropic dropped a report this week saying it disrupted a Chinese state-linked espionage campaign that used the company’s Claude Code product to target around 30 organisations. The group circumvented guardrails by breaking down the campaign into individual tasks and telling Claude it was conducting a security audit. (No, really!) Only a “small number” were actually compromised. News of the report spread quickly, fuelled by the idea of AI conducting cyber intrusions automatically. Anthropic says in their report that AI performed “80-90%” of the activity, and when they say ‘performed’, they mean Claude Code acted as an automation layer, firing off requests to open source tools, digesting output, and so on. There was a lot of human work that went into setting up these tools, their APIs, and related components. The AI-assisted data parsing, but it wasn’t crafting novel tools or acting of its own volition, and it deferred to humans 4-6 times per organisation. If I were being unfair, I’d say this was a batch script with some [Y/N] prompts, but, regardless of scepticism, there’s a clear direction of travel here. Naturally, Anthropic says it’s disrupted the campaigns, and that the only way to defend against this kind of thing is with AI defence, too. NEWS, REPORT, SCEPTICISM
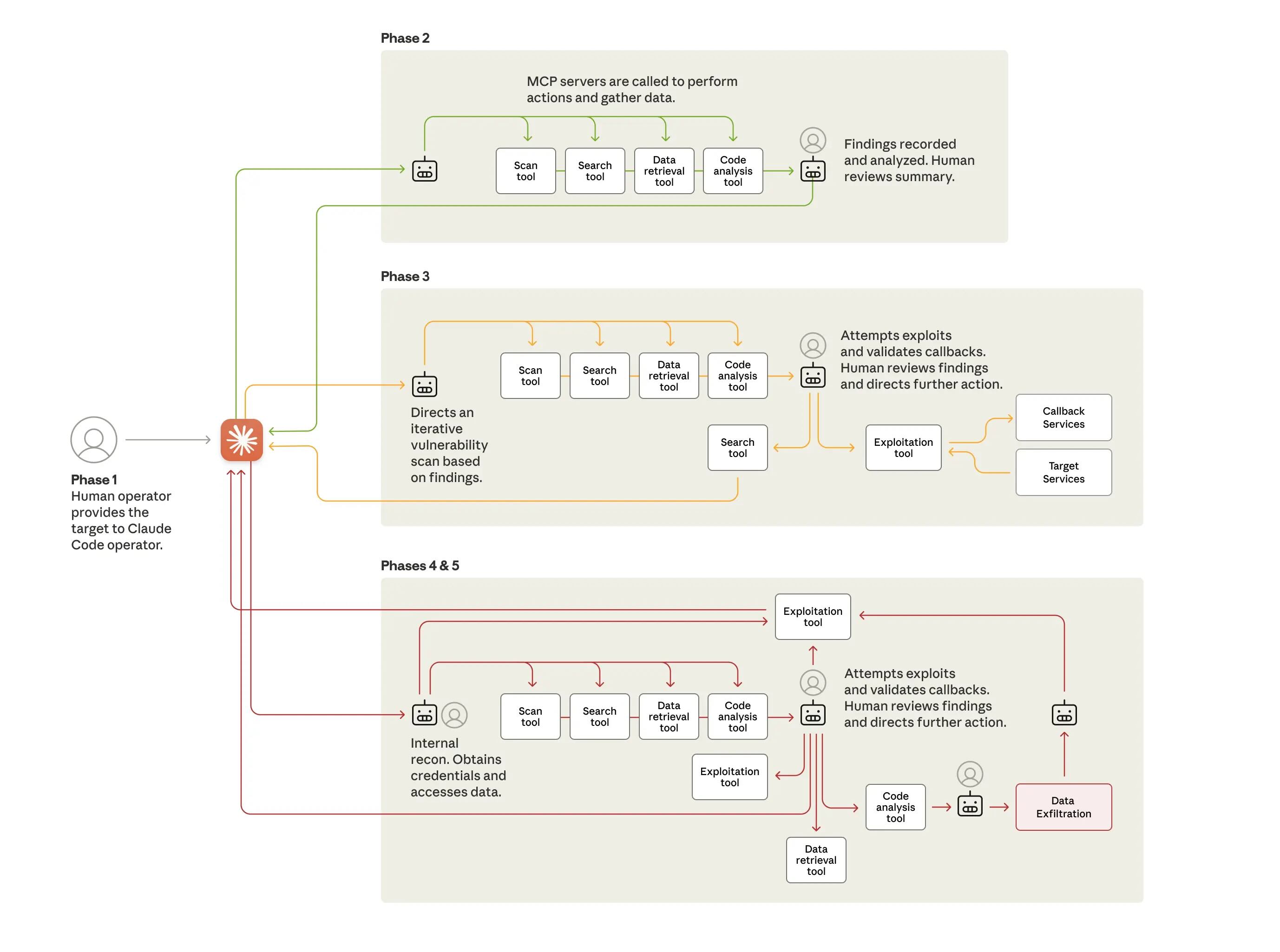
-
Cyber Security and Resilience Bill: The UK’s Cyber Security and Resilience (CSR) got its first outing in Parliament this week. It’s been four years in the making and represents an update to the NIS regulations introduced in 2018. The headline reporting timeframe for “more harmful” incidents to NCSC will be 24 hours, with a full report of what’s happened within 72 hours. The CSR brings data centres and IT managed service providers (MSPs) into the scope of regulation. EV charging networks and smart home heating appliances will also face new rules. Further powers for regulators are included, with the (now typical) penalties of 10% turnover or £17 million (whichever is greater), but extending to daily £100,000 fines for persistent contraventions. The economic impact of businesses implementing CSR measures is estimated at up to £590 million. CSR, MORE, GOV.UK
-
OWASP Top 10: The Open Worldwide Application Security Project (OWASP) published an updated Top 10 application security issues this week. Broken Access Control retains the ‘top’ spot, followed by Security Misconfiguration and Software Supply Chain Failures, which are both up three places. The “data-driven awareness document” was previously updated in 2021 and is intended to help organisations prioritise security in their applications. NEWS, TOP 10

-
Jaguar Land Rover: The UK statistics authority cited a “28.6% fall in the manufacture of motor vehicles” as a reason for lower-than-expected UK economic figures this week. UK GDP (Gross Domestic Product) expanded by just 0.1% in the July-September quarter, down from 0.3% in the previous quarter, and lower than analyst expectations of 0.2%. I believe it’s the first time a cyber-attack has been cited in country-level macro-economic reporting. That’ll get some bragging rights for the (likely) ‘kids’ behind the attack, but I’d not want to be on the receiving end of that kind of law enforcement heat. Also this week, JLR reported £196 million in direct costs associated with responding to the incident, alongside a pre-tax loss of £485 million for the three months to 30th September (the same period a year prior reported a £398 million profit). GDP, JLR
-
Synnovis is beginning to notify people affected by the June 2024 Qilin ransomware attack that disrupted the firm’s NHS blood testing services. The (count them), seventeen months to notify is because the “compromised data was unstructured, incomplete and fragmented, and often very difficult to understand”. Meanwhile, Clop added the NHS to its leak site on 11th November, though the nature of which part of the UK’s health system has been affected is unknown, and no data has been leaked. SYNNOVIS, NHS
Startup spotlight
As part of my pledge to support the UK cyber ecosystem, I’ll be featuring a different UK cyber startup each week.
If you’re a UK-based cyber security startup interested in being featured in a ‘Startup Spotlight’ in my weekly newsletter, please fill out this form for consideration. It’s not a paid thing; just trying to support our ecosystem 🚀
And finally
- Checkout.com’s CTO has confirmed a ransomware incident, with the company refusing to pay the ransom demands, and instead making a comparable donation to cybercrime research. CHECKOUT